Connect via HTTPS
Configure your agentgateway proxy to connect to an MCP server by using the HTTPS protocol.
About this guide
In this guide, you configure your agentgateway proxy to connect to the remote GitHub MCP server by using the HTTPS protocol. The server allows you to interact with GitHub repositories, issues, pull requests, and more. All connections to the server must be secured via HTTPS and a GitHub access token must be provided for authentication.
Before you begin
Set up an agentgateway proxy.
Connect to the MCP server
-
Create a personal acess token in GitHub and save it in an environment variable. For more information, see the GitHub docs.
export GH_PAT=<personal-access-token> -
Create a Backend for the remote GitHub MCP server. The server requires you to connect to it by using the HTTPS protocol. Because of that, you set the
mcp.targets.static.portfield to 443.kubectl apply -f- <<EOF apiVersion: gateway.kgateway.dev/v1alpha1 kind: Backend metadata: name: github-mcp-backend namespace: kgateway-system spec: type: MCP mcp: targets: - name: mcp-target static: host: api.githubcopilot.com port: 443 path: /mcp/ EOF -
Create a BackendTLSPolicy to configure your agentgateway to connect to your Backend by using HTTPS. To validate the MCP server’s TLS certificate, you use the well-known system CA certificates. Note that to use the BackendTLSPolicy, you must have the experimental channel of the Kubernetes Gateway API version 1.4 or later.
kubectl apply -f- <<EOF apiVersion: gateway.networking.k8s.io/v1 kind: BackendTLSPolicy metadata: name: github-mcp-backend-tls namespace: kgateway-system spec: targetRefs: - name: github-mcp-backend kind: Backend group: gateway.kgateway.dev validation: hostname: api.githubcopilot.com wellKnownCACertificates: System EOF -
Create an HTTPRoute that routes traffic to the GitHub MCP server along the
/mcp-githubpath. To properly connect to the MCP server, you must allow traffic fromhttp://localhost:8080, which is the domain and port you expose your agentgateway proxy on later. If you expose the proxy under a different domain, make sure to add this domain to the allowed origins. Because the MCP server also requires a GitHub access token to connect, you set theAuthorizationheader to the token that you created earlier.kubectl apply -f- <<EOF apiVersion: gateway.networking.k8s.io/v1 kind: HTTPRoute metadata: name: mcp-github namespace: kgateway-system spec: parentRefs: - name: agentgateway rules: - matches: - path: type: PathPrefix value: /mcp-github filters: - type: CORS cors: allowHeaders: - "*" allowMethods: - "*" allowOrigins: - "http://localhost:8080" - type: RequestHeaderModifier requestHeaderModifier: set: - name: Authorization value: "Bearer ${GH_PAT}" backendRefs: - name: github-mcp-backend group: gateway.kgateway.dev kind: Backend EOF
Verify the connection
Use the MCP Inspector tool to verify that you can connect to your sample MCP server through agentgateway.
-
Get the agentgateway address.
export INGRESS_GW_ADDRESS=$(kubectl get gateway agentgateway -n kgateway-system -o=jsonpath="{.status.addresses[0].value}") echo $INGRESS_GW_ADDRESSkubectl port-forward deployment/agentgateway 8080:8080 -n kgateway-system -
From your terminal, run the MCP Inspector command to open the MCP Inspector in your browser. If the MCP inspector tool does not open automatically, run
mcp-inspector.npx modelcontextprotocol/inspector#0.16.2 -
From the MCP Inspector menu, connect to your agentgateway address as follows:
- Transport Type: Select
Streamable HTTP. - URL: Enter the agentgateway address, port, and the
/mcp-githubpath. If your agentgateway proxy is exposed with a LoadBalancer server, usehttp://<lb-address>:8080/mcp-github. In local test setups where you port-forwarded the agentgateway proxy on your local machine, usehttp://localhost:8080/mcp-github. - Click Connect.
- Transport Type: Select
-
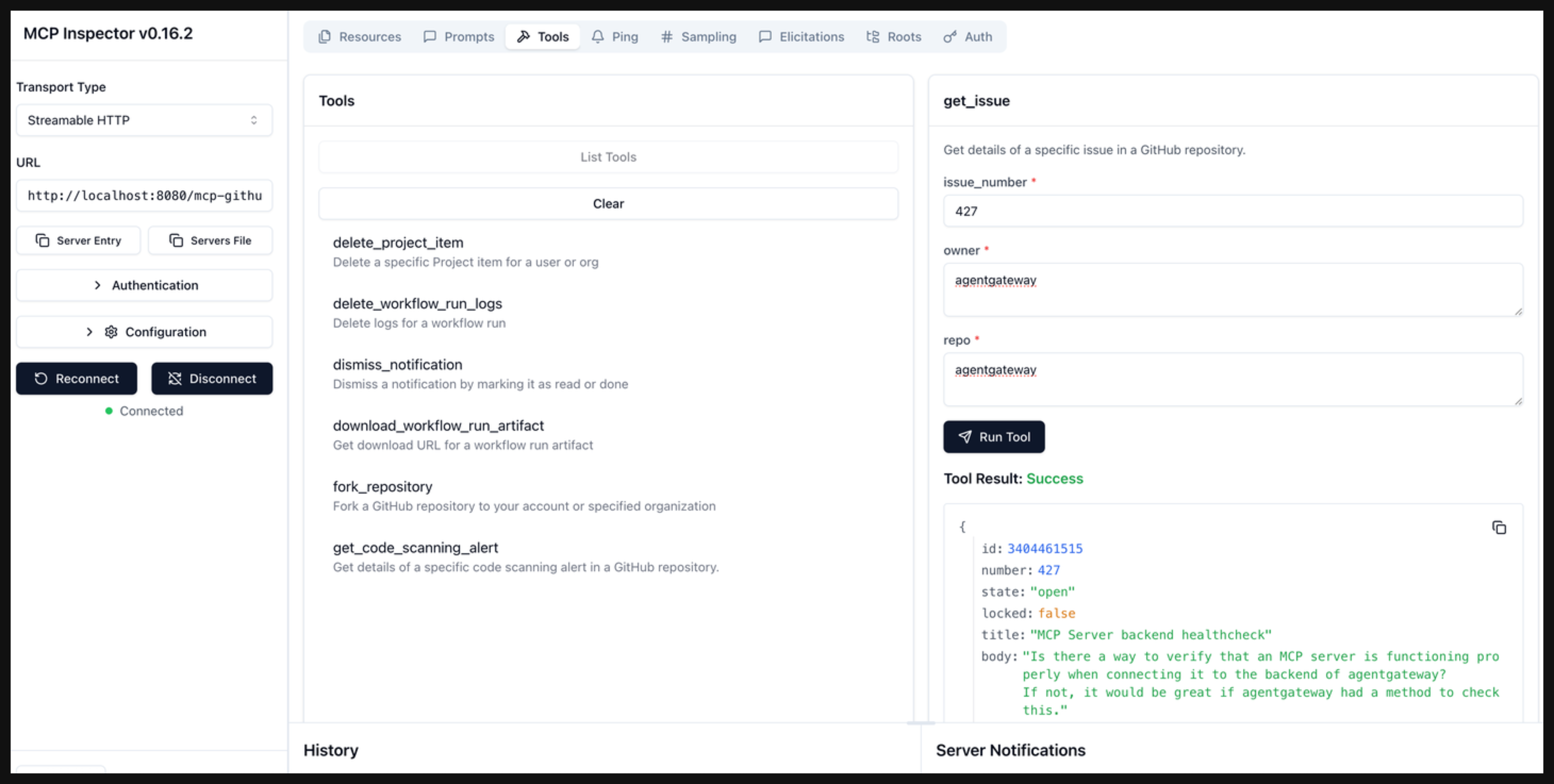
From the menu bar, click the Tools tab. Then from the Tools pane, click List Tools and select the
get_issuetool. -
From the get_issue pane, enter the following details, and click Run Tool.
issue_number: 427owner: agentgatewayrepo: agentgateway
-
Verify that you get back the fetched issue content.
Cleanup
You can remove the resources that you created in this guide.kubectl delete Backend github-mcp-backend -n kgateway-system
kubectl delete BackendTLSPolicy github-mcp-backend-tls -n kgateway-system
kubectl delete HTTPRoute mcp-github -n kgateway-system